Securing East-West Traffic in a Container-based Data Center
Enterprise applications moving into the cloud, either public or private, is one of the most prominent trends in the tech industry. A lot of attention has been placed on how to setup the data center environment and deploy applications in recent years, but little attention has been paid to securing east-west traffic.
As the infrastructure became mature through innovations in server technology, switch design and network and storage virtualization, securing the applications and data in the data center has become the top priority for many IT managers.
To understand the differences between the traditional network security model and the security in the data center, it’s important to recognize the network traffic patterns in the data center. Traffic in data center typically flows in three directions. Traffic entering or exiting from the data center is called north-south traffic. On the other hand, east-west traffic refers to the network communications between servers and applications within the data center. Many enterprise and financial services companies have traffic flowing between multiple private and public clouds they manage.
Because of the multi-tier design of today’s enterprise applications, the east-west direction typically accounts for 70% of all network traffic in the data center.
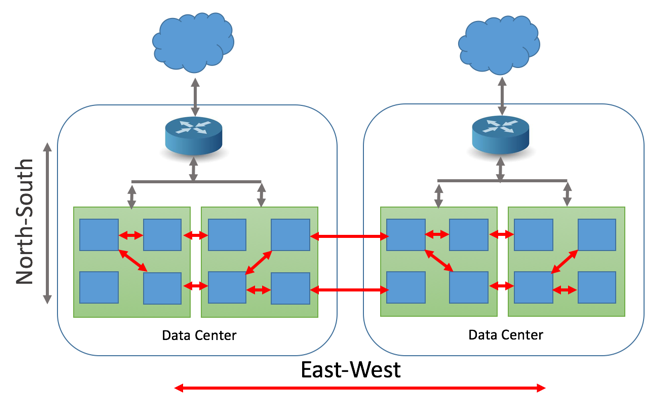
With the adoption of a micro-service architecture and container technology in modern applications, the portion of east-west traffic will only grow larger. As monolithic applications are broken into pieces, functions previously achieved by RPC calls and domain sockets are replaced by packets on the wire.
Obviously, traffic across data center boundaries over the Internet need to be secured. Most enterprises have at least some NGFW, IPS, WAF, and DDoS mitigation devices deployed at the entrance of their data centers. Inter data center traffic is often further secured by IPSec.
At the same time, east-west traffic security within a data center is often neglected.
“As long as the perimeter is protected, I don’t have to worry about the internal security, right?”
In fact, according to some research reports, about half of the security breaches are caused by insiders, within the data center. A compromised mobile device can introduce malware when accessing the internal data. Sensitive data can be stolen if egress policies are not well defined. Packaged application images may contain unknown vulnerabilities. And malware can spread within a data center rapidly if the internal network is not protected throughout, from the web servers to business logic and databases. Surprisingly, these attacks can bypass layered protections at the data center entrance because these devices have no idea of what and how things are running within.
“Would you hire a security team to guard your building if they don’t know how the rooms and corridors are arranged?”
There have been several attempts that try to solve the data center’s internal security issues. However, many of them still employ the bulky hardware oriented designs, attaching the security enforcement point to hardware devices or rerouting the network traffic to some centralized nodes. These solutions are heavy and slow, and almost always become the bottleneck of the network.
It’s especially unacceptable in a containerized environment. Containers are more short-lived compared to virtual machines. If a container causes damage and get killed after a short while, it probably leaves no trace at all if the security solution has no awareness of the container life cycle. If a security solution cannot scale fast enough to keep up with the applications, those applications are left unprotected at their most critical moments. After all, the most important benefits that container technology brings to us are its easiness to deploy and scale. Deploying container security should not be a burden to DevOps, otherwise, no one would be willing to use it.
Although securing east-west traffic is generally thought of within a data center, you could imagine east-west traffic even between data centers. When there are private networks or hybrid public-private clouds, not all traffic between data centers might flow north-south. This might even occur more frequently with containers, since it’s so easy to deploy and destroy containers based on the best available resources. East-west traffic between containers in different data centers could also be a vulnerable point.
So, in order to secure east-west traffic it looks like we are asking for contradictory things. On one hand, a security solution must be solid, reliable and sophisticated enough. At the same time, it should be lightweight, scale well within or across data centers and understand your container deployment and application behavior. Providing a security solution that satisfies both issues is a challenge for the security industry. It is especially difficult to achieve in a containerized environment.

Related Articles
Apr 10th, 2025
Why You Should Be Using A Kubernetes Security Platform
May 27th, 2024