How to Protect Sensitive Data in Containers with Container DLP
We recently announced the industry’s first Container DLP capability to help enterprises protect sensitive data. Let’s take a deeper look into data loss prevention (aka data leak protection) and how it applies to containers.
What is Data Loss Prevention (DLP)?
DLP solutions help detect potential sensitive data violations and prevent accidental or malicious data breaches. Sensitive data is anything that a company considers private or confidential. Common types of sensitive data protected by regulatory compliance include credit cards (PCI), personally identifiable information (PII, GDPR), patient information (HIPAA), social security and other government identities. Financial account and bank routing information is also considered sensitive data. Sensitive data can even include documents, drawings, contracts or other business and technical documents.
DLP solutions can involve a broad spectrum of potential systems including servers, databases, networks, laptops, desktops and email systems. For container DLP most of the current concern would be for applications that process, transmit, or store sensitive data because containers are primarily deployed for enterprise applications. In addition, containers themselves may store sensitive data such as secrets used to access applications, even though it is recommended to use a secure secrets management solution for this purpose.
Ways to Protect Data
Like all of security, a layered approach to DLP is recommended, and the extent of monitoring and controls required depends on the type of sensitive data involved as well as regulatory compliance requirements.
Encryption
The most basic preventative measure to be taken is encryption to make sure that all sensitive data, whether at rest in file systems or databases, or in motion being transmitted is protected. Most regulatory compliance standards require encryption.
Container DLP requires that connections between pods – ie east-west traffic between containers – be encrypted when transmitting sensitive data. Connections into and out of (ingress and egress) the container cluster should also be encrypted if they contain sensitive data. For pod to pod connections, new service mesh technologies like Istio offer a simple and scalable encryption solution. In addition to network connections, any storage accessed or written to by the container must encrypt the data at rest.
Detection
The encryption requirements are fairly straight forward, but how do you make sure there’s not a data breach or unintentional transmission of unencrypted sensitive data? The most effective way is to monitor the network for sensitive data. Additionally, periodic file and database scanning solutions can make provide an added layer of security for data at rest.
Network-based Container DLP
Detecting sensitive data in network connections is the most effective way to prevent data breaches and insure regulatory compliance. Network-based container DLP requires layer 7 (application layer) deep packet inspection to be able to inspect the network payloads for sensitive data.
The NeuVector container network security platform is an end-to-end solution for securing the entire container pipeline from build to ship to run-time. The industry’s first container firewall provides the critical function to perform container DLP by inspecting all container connections for sensitive data such as credit cards, PII, and financial data. The screen shot below shows an example of unencrypted credit card data being transmitted between pods, as well as to an external destination.
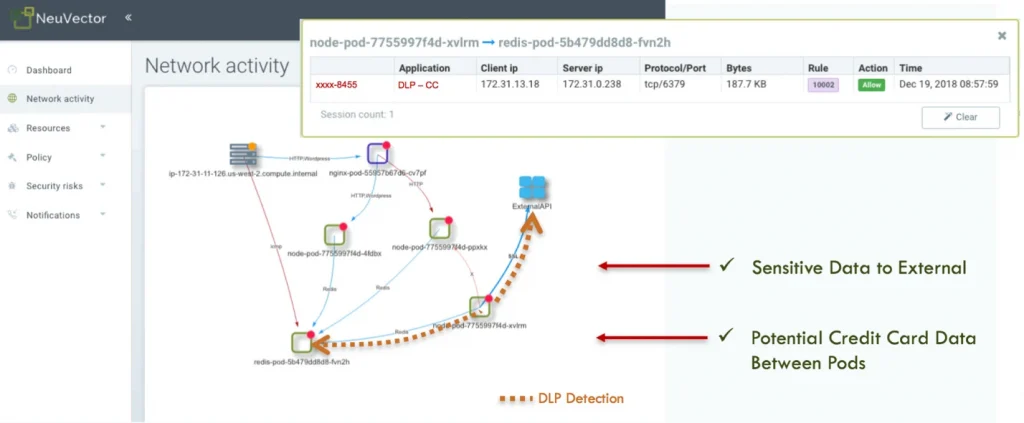
DETECTING CREDIT CARD DATA VIOLATIONS IN CONTAINER CONNECTIONS
The NeuVector container firewall detects this violation and can block this transmission in in Protect mode, or alert on it if in Monitor mode.
The NeuVector container DLP engine is flexible and extensible to be able to detect multiple types of sensitive data patterns and can be customized for customer specific detection.
Regulatory Compliance – PCI, GDPR, HIPAA etc
A container DLP solution can be used to meet regulatory compliance requirements by providing network segmentation, network monitoring, and encryption verification. PCI-DSS requires network segmentation as well as encryption for in-scope CDE environments. The NeuVector container firewall with DLP can provide the required network segmentation of CDE workloads while at the same time monitoring for unencrypted cardholder data which would violate the compliance requirements. The violations can be the first indications of a data breach, a misconfiguration of an application container, or an innocent mistake made by a customer support person pasting in credit card data into a case.
NeuVector can help maintain compliance to regulations such as PCI-DSS, GDPR, HIPAA and others for container deployments by:
- Enforcing network segmentation based on layer 7 application protocols, so that no unauthorized connections are allowed in or out of containers
- Enforcing that encrypted SSL connections are used for transmitting sensitive data between containers and for ingress/egress connections
- Monitoring all unencrypted connections for sensitive data and either alerting or blocking when detected
In addition, through a service mesh integration, NeuVector can even alert if any sensitive data is included even in encrypted connections between service mesh pods. NeuVector is able to inspect the network traffic before it is encrypted by the service mesh sidecar proxy and detect threats as well as sensitive data in the payload. This is useful for detecting cases where sensitive data should not exist at all, even if it is encrypted by the service mesh.
Related Articles
Feb 15th, 2023
Stop the Churn with SUSE eLearning
Feb 01st, 2023
Kubernetes Security: Vulnerability Management
Feb 01st, 2023
Container Security: Network Visibility
Oct 28th, 2022